Automating network security entails using technology to detect, investigate, and mediate network security threats. Typically, software and other tools are deployed to perform security administrative duties such as configurations, monitoring networks for malicious activities, and handling threats that may occur. This is typically done with little or no human intervention.
Automating network security allows organizations to scale and handle many threats, thus avoiding overloading security teams. Additionally, it helps organizations comply with changing network security laws and policies and avoid misconfiguration errors that occur when human labour is used to handle configurations of security of networks.
Automation also facilitates faster, real-time threat detection and mitigation, thus improving the efficiency of a network’s security. This also leads to higher accuracy and consistency in handling threats, thus minimizing damage and saving time and costs for an organization.
Generally, network security automation helps organizations improve their overall security, avoiding costly data breaches and cyber-attacks. Now, let’s understand Security Content Automation Protocol (SCAP).
What is SCAP?
Security Content Automation Protocol (SCAP) provides standards and protocols designed to organize, express, and measure security-related information, security configuration issues, and post-compilation software flaws in standardized ways. SCAP is essentially a checklist that organizations follow to improve their security.
To organizations, SCAP helps them automate the process of checking for known vulnerabilities, automating the verification of security configuration settings, and generating reports that link low-level settings to high-level requirements. As a result, it helps improve an organization’s security, effectively reducing cyber-attacks and data breaches.
Benefits of SCAP
Organizations stand to benefit a lot from implementing SCAP. Some of these benefits include:
Enterprise systems must constantly comply with regulations and be secure to minimize attacks and data breaches. Implementing SCAP is thus a good way to ensure they comply with regulations and have very secure systems that can prevent, detect and mitigate threats efficiently.
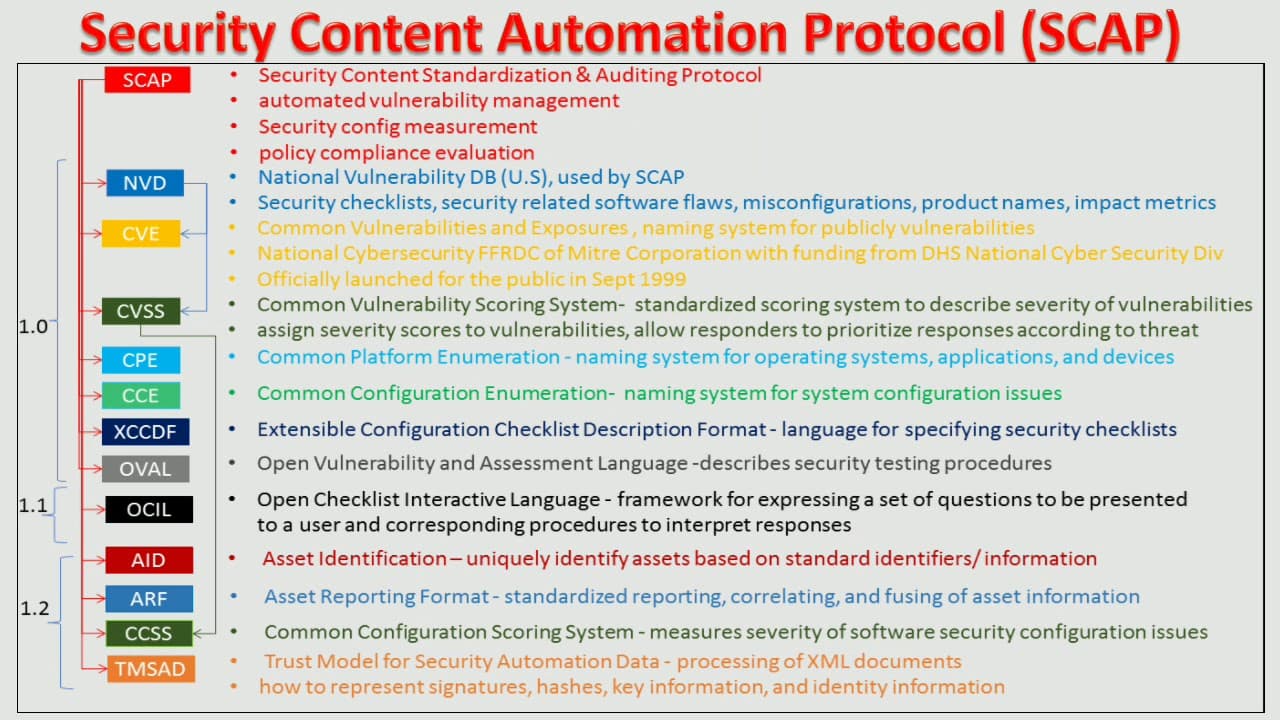
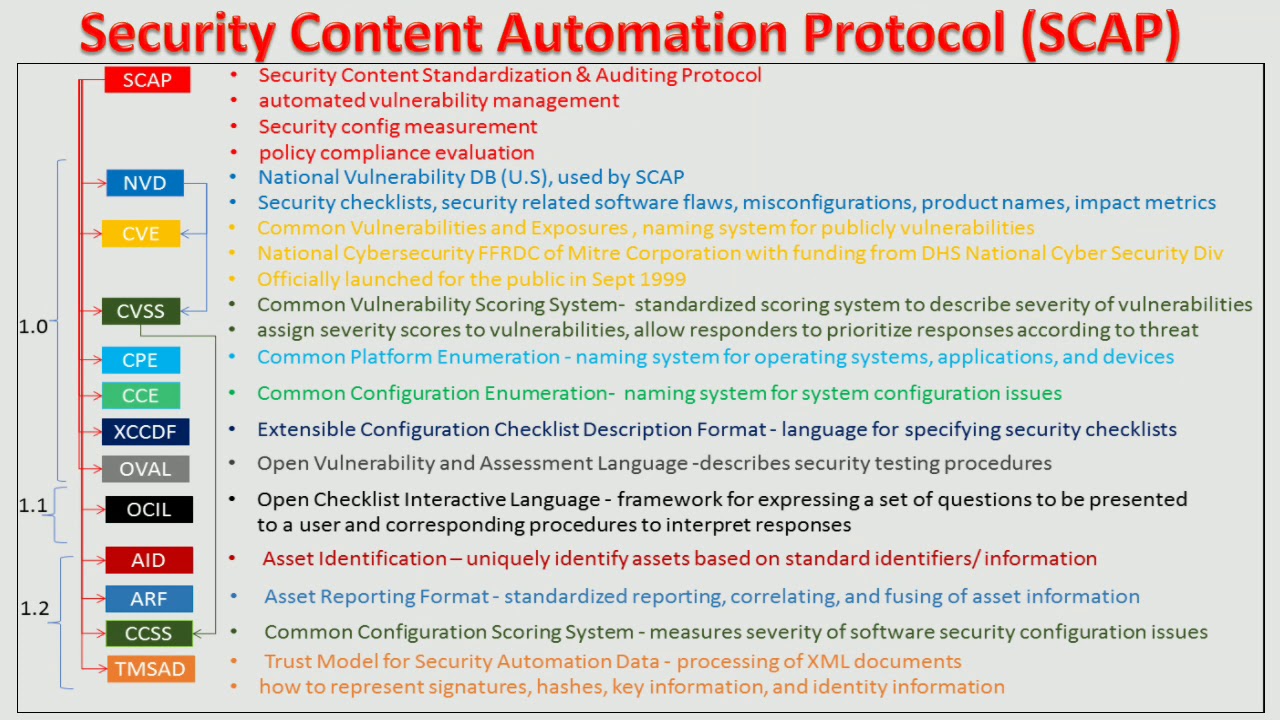
SCAP Components
A key element in SCAP is a protocol standardizing how software communicates information about software flaws and security configuration. These specifications are also referred to as SCAP components. SCAP components include:
The listed SCAP components are what SCAP uses to standardize the communication of software flaws and configurations.
Why is SCAP Important
Any organization stands to reap huge benefits by using SCAP. First, SCAP provides a standardized framework that an organization can use to evaluate and manage its security, ensuring that its systems are sufficiently secured.
Since SCAP is used to evaluate organizations’ compliance with security regulations, SCAP allows organizations to comply with existing regulations and policies, avoiding penalties. To cap it all, SCAP helps organizations save on cost and manpower and improve their security.
For any organization keen on security and compliance with regulations, SCAP is a must-have. Consider the following resources to learn more about SCAP and how it can help your organization.
Security Content Automation Protocol: Step-By-Step Guide
This book on Security Content Automation Protocol, available as a paperback version, offers an in-depth self-assessment that organizations and security professionals can use to improve their understanding of the requirements and elements of the SCAP.
https://www.amazon.com/dp/0655427465?tag=geekflare-20&linkCode=ogi&th=1&psc=1
The book provides a tool that facilitates a rapid self-assessment to determine the level of correspondence between an organization’s existing management practices and procedures and what SCAP requires.